AI Regulatory Compliance: Why Keeping Tabs on HIPAA & GDPR Matters
Data protection, privacy, and AI regulatory compliance are becoming increasingly vital as our lives grow more data-driven — and as unauthorized parties become more eager to access sensitive information that doesn't belong to them.

Today, we shop online, connect via social media, store personal memories in the cloud, and rely on a growing number of apps that collect and process our data. This digital convenience brings undeniable benefits but it also raises serious concerns around privacy and data security.
As data breaches become more frequent, the risk to our personal information continues to grow. In 2023, Europe led with 116.6 million breaches (44% of the global total), while North America rose sharply from 34.7M in 2022 to 101.7M, becoming the 2nd most affected region. In 2024, the average data breach cost hit $4.88 million.

Yet many organizations remain underprepared. According to a recent Ponemon Institute report, just 56% of companies have a formal plan to respond to data breaches — and even fewer routinely update those plans. Meanwhile, regulatory bodies like the Federal Trade Commission (FTC) are ramping up enforcement around data privacy practices.
Around the globe, governments are introducing stricter data protection law and AI regulatory compliances designed to give individuals greater control over their personal information and to hold organizations accountable for safeguarding it. This isn't just a local challenge. While the EU's GDPR remains a global benchmark, countries like Australia, Canada, and Argentina have also rolled out robust data privacy frameworks.
In this article, we break down:
- the core principles behind major compliance frameworks
- the key regulations businesses need to know
- how these laws apply in real-world business scenarios
- and what sets them apart from one another.
...or simply grab instant access to our guide and get up to speed fast.
What is the GDPR?
The General Data Protection Regulation (GDPR), which came into effect on May 25, 2018, remains one of the most comprehensive and far-reaching data privacy laws in the world. It governs how organizations collect, store, and process personally identifiable information (PII) of individuals in the UK and EU — regardless of where the organization itself is located.
Under the AI and GDPR, organizations must implement and thoroughly document protocols to protect personally identifiable information (PII). These documented measures should include:
— Consent. Whenever data is repurposed, organizations must obtain fresh consent from individuals.
— Breach notifications. Organizations have a strict 72-hour window to notify affected individuals of any data breach — whether via email, phone, or public announcement.
— Right to access. Organizations must clearly inform UK and EU residents how their personal data is being used.
— Right to be forgotten. Unless legally obligated to retain it, organizations must promptly delete an individual's PII upon request and stop any further sharing or processing of that data.
— Privacy by design. Data processing should be limited strictly to what is necessary to fulfill the organization's business purpose, embedding privacy protections into systems and processes from the outset.
AI and GDPR: Who Must Comply with the GDPR?
The GDPR applies to any entity that meets one or more of the following criteria:
✅ Has a physical presence in the EU. In this case, the organization must apply GDPR protections to all users, not just EU residents.
✅ Offers goods or services to individuals in the EU. This includes free offerings such as apps, newsletters, or online platforms.
✅ Monitors the behavior of individuals in the EU. This could involve tracking user activity, profiling, or using cookies to observe how people interact with a website or service. For example, a provider based in the U.S. must comply with the GDPR if it processes the personal data of users located in the EU.
Failure to comply with the GDPR can lead to steep penalties — up to €20 million, or 4% of your global annual revenue. For instance, Facebook (now Meta) has faced multiple investigations and set aside $3 billion in anticipation of GDPR-related fines. Facebook paid a $645,150 fine for the Cambridge Analytica scandal, which occurred before the GDPR came into effect. However, the company remains under investigation for additional potential penalties related to ongoing data privacy concerns.
📝 A common misconception is that the GDPR only applies to companies based in Europe. In reality, it has an extraterritorial scope: any business, non-profit, or government agency anywhere in the world that processes the data of individuals in the EU or UK may fall under its jurisdiction.
This includes organizations that offer goods or services to individuals in the EU, or monitor their online behavior — even if they don't have a physical presence in Europe. For example, a company conducting research or running surveys that collect data from EU residents must still comply with GDPR requirements.
Many companies start their GDPR journey by focusing on what's most visible to customers and partners:
Adding a cookie banner to their website → Publishing a Privacy Policy → Including consent checkboxes on contact or registration forms.
For mobile apps, platforms like Google Play and the App Store require Terms of Use and a compliant Privacy Policy before approval. Businesses often prepare these documents early, assuming that compliance is "done." But this approach is like cleaning up a storefront — great for appearances, but what about behind the scenes?
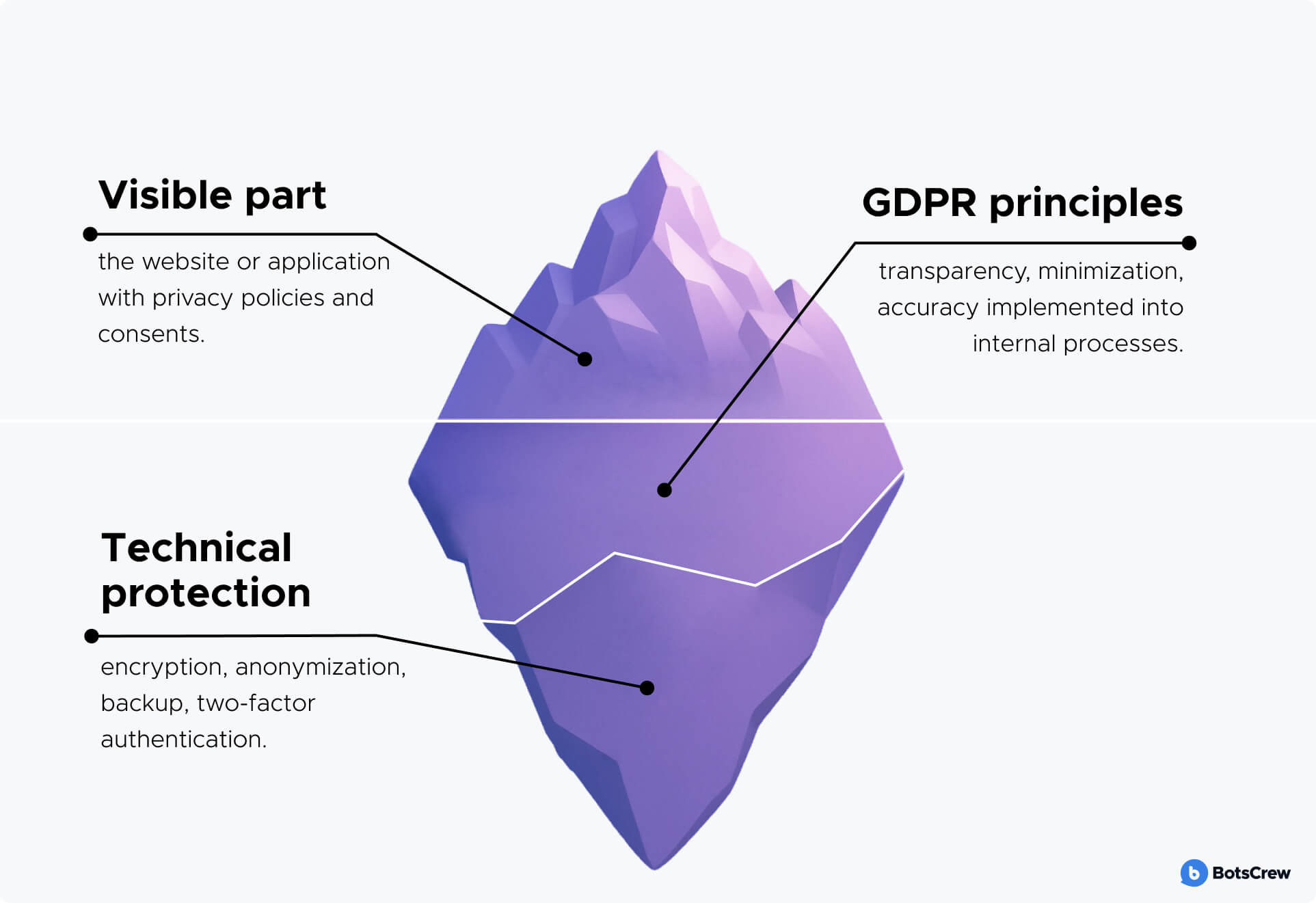
GDPR has 3 layers:
1️⃣ The Visible Layer — what users see. This includes cookie banners, privacy policies, and consent forms. However, even here, mistakes are common. For example, many companies ask for consent when it's not needed (for processing data under a contract), leading to unnecessary complexity and potential non-compliance.
2️⃣ Principles and User Rights — what guides the process. GDPR is built on key principles that must be embedded into how personal data is collected and processed:
- Transparency & Lawfulness: Explain clearly what data is collected, why, on what legal basis, and for how long.
- Minimization: Collect only what's necessary and limit access to those who genuinely need it.
- Accuracy: Ensure data remains current and give users the ability to correct inaccuracies.
3️⃣ Technical Safeguards — what users don't see. The core of accurate GDPR compliance lies in how securely data is handled behind the scenes:
- Encrypt data, especially in transit
- Limit access with strong controls
- Use pseudonymization or anonymization
- Maintain regular backups
- Enforce two-factor authentication
Real GDPR compliance isn't just about looking good on the surface — it is about building trust through responsible, transparent, and secure Generative AI and data practices at every level of your organization.
What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, serves as a foundational law for protecting healthcare data in the U.S. While often associated with patient privacy, HIPAA is far broader in scope — it governs how sensitive personal health information is accessed, stored, used, and shared across the entire healthcare ecosystem.
At its core, HIPAA was designed to modernize the flow of healthcare information, set standards for handling protected health information (PHI), and reduce healthcare fraud and abuse. In doing so, it also created a framework that holds organizations accountable for data privacy and security.
Who Must Comply with HIPAA?
HIPAA applies to two main groups:
✅ Covered Entities. These include:
- Healthcare Providers: Doctors, clinics, hospitals, pharmacies, dentists, etc.
- Health Plans: Insurance companies, HMOs, Medicare, Medicaid, employer-sponsored health plans.
- Healthcare Clearinghouses: Organizations that process non-standard health information into a standardized format.
✅ Business Associates. Any third party that performs activities involving the use or disclosure of PHI on behalf of a covered entity. This includes:
- Cloud service providers
- Data hosting platforms
- Medical billing services
- Software vendors
- Legal, actuarial, or administrative consultants.
Business associates are directly liable under HIPAA, and must sign a Business Associate Agreement (BAA) with covered entities to define responsibilities and liabilities.
Protected Health Information (PHI) includes any identifiable data that relates to an individual's:
- Medical history
- Diagnoses and treatments
- Lab results
- Insurance details
- Billing information
- Mental health records
- Biometric identifiers
- Contact details (when associated with health data)
When stored or transmitted electronically, this data is referred to as ePHI and is subject to additional security provisions.
The Three Pillars of HIPAA Compliance
HIPAA is enforced through three primary rules, each with its own set of obligations:
1️⃣ Privacy Rule. Defines strict boundaries for how PHI can be used and shared. Patients have the right to: access their medical records, request corrections, receive a list of disclosures, request limits on certain uses, and obtain privacy notices from providers.
2️⃣ Security Rule. Requires entities to protect electronic PHI (ePHI) with both technical and non-technical safeguards, including access control and encryption, secure data transmission, regular risk assessments, and staff training on cybersecurity.
3️⃣ Breach Notification Rule. In the event of a data breach, affected individuals must be notified within 60 days unless fewer than 500 individuals are impacted — then an annual summary is allowed. Larger breaches must also be reported to the Department of Health and Human Services (HHS) and, in some cases, to the media.
HIPAA is enforced by the U.S. Department of Health and Human Services' Office for Civil Rights (OCR). Fines vary based on the severity of the violation, ranging from $100 to $50,000 per incident, with an annual cap of $1.5 million per violation category.
However, in practice, settlements and fines can be far higher, especially in egregious or repeat cases. A few examples:
Anthem Inc. (2018): Paid $16 million after a massive breach compromised the data of nearly 79 million people.
Premera Blue Cross (2020): Fined $6.85 million for a breach affecting 10.4 million individuals.
These cases highlight the importance of not only building compliant systems but actively monitoring, testing, and updating them.
HIPAA Compliance Checklist
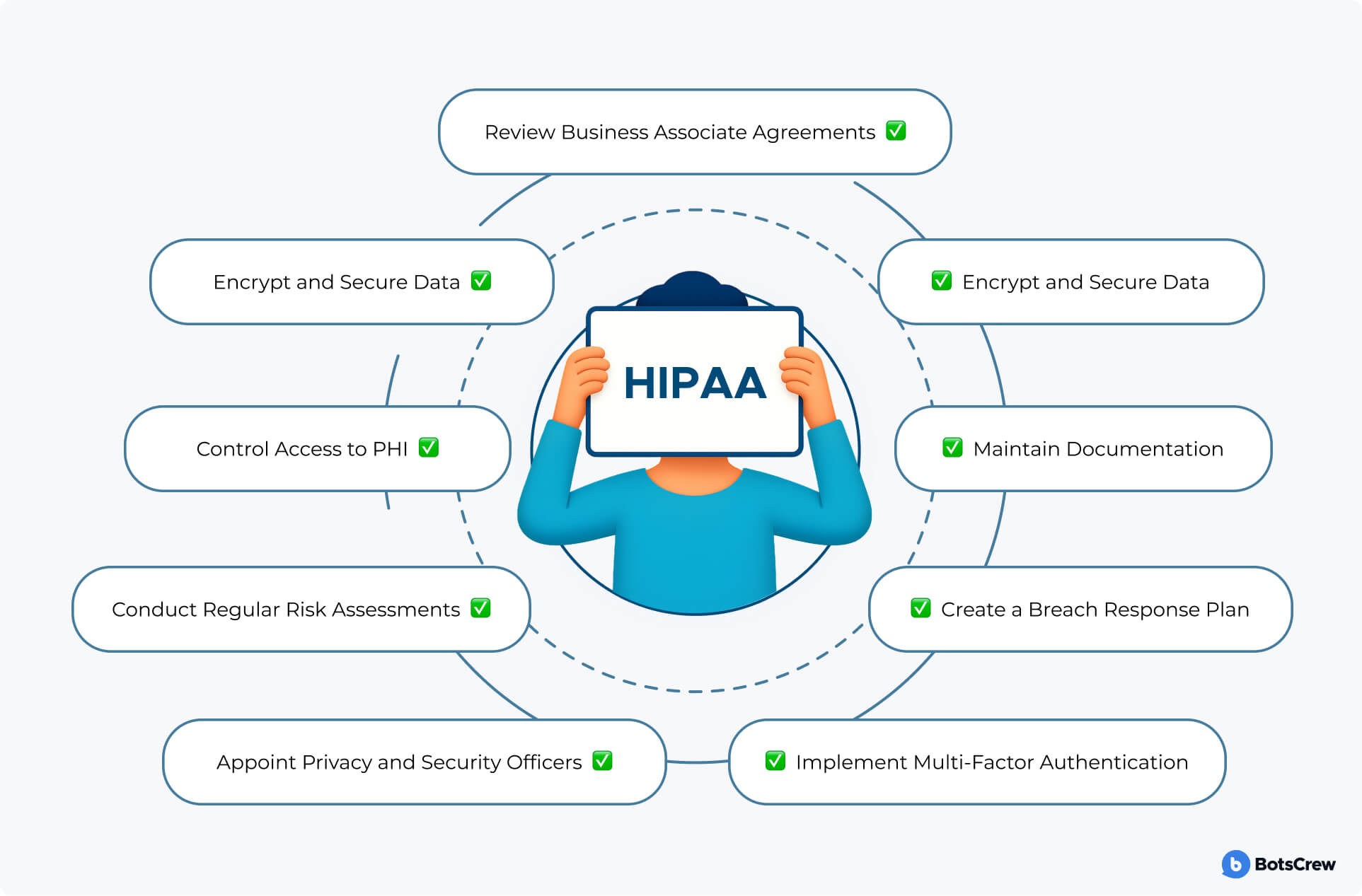
What every organization must consider working on HIPAA AI compliance:
#1. Appoint Privacy and Security Officers. HIPAA mandates two critical roles: a Privacy Officer (to oversee policy and patient rights) and a Security Officer (to implement technical safeguards). These individuals are responsible for ensuring ongoing compliance and organizing staff training.
#2. Conduct Regular Risk Assessments. An annual risk analysis is mandatory. It should identify vulnerabilities in data storage, access, transmission, and backup procedures. The findings must guide actionable improvements.
#3. Control Access to PHI. Only authorized personnel should be able to access PHI. Implement role-based access controls, enforce strong password protocols, and log all access to sensitive data.
#4. Encrypt and Secure Data. All ePHI must be encrypted — both at rest and in transit. Additionally, backup systems should be in place and tested regularly to ensure data recovery in case of breaches or outages. Any device that accesses PHI — phones, laptops, tablets — must be protected with encryption, password locks, and remote wipe capabilities in case of theft or loss.
#5. Implement Multi-Factor Authentication. Two-factor authentication (2FA) significantly reduces the risk of unauthorized access and is considered a best practice under the Security Rule.
#6. Create a Breach Response Plan. You must have a documented procedure for detecting, reporting, and managing breaches. Include internal communication, patient notification protocols, and contact with OCR.
#7. Maintain Documentation. Keep records of all compliance efforts, including:
- Risk assessments
- Audit results
- Security incidents
- Training attendance
- Consent forms and authorizations
#8. Review Business Associate Agreements (BAAs). Ensure every third-party vendor handling PHI signs a BAA. Review these agreements regularly to reflect any changes in services or responsibilities.
The Newest Changes to HIPAA
In 2022, the HHS proposed updates to HIPAA to strengthen individual rights. Among the key changes:
- Response time for PHI requests reduced from 60 to 30 days
- More clarity on electronic access rights
- Easier methods for patients to direct the transfer of their data to other providers.
🚨 Privacy isn't optional. Fines are real. Avoid costly penalties and reputational damage with a proactive compliance strategy. Schedule a call, and we'll walk you through how our AI agents keep data secure and regulators satisfied.
What is PIPEDA?
The Personal Information Protection and Electronic Documents Act (PIPEDA) is Canada's federal privacy law for the private sector. Enacted in 2000 and effective from 2001, it governs how businesses collect, use, and disclose personal information during commercial activities.
PIPEDA defines “personal information” broadly — it includes identifiers (name, address, ID numbers), demographics, financial data, health records, employment details, and even contextual data used to identify individuals.
Who Must Comply with PIPEDA?
PIPEDA applies broadly across Canada, but compliance requirements vary depending on the type of organization, the nature of the business activity, and the jurisdiction under which it operates.
✅ Private-Sector Organizations Engaged in Commercial Activities. PIPEDA governs all private-sector organizations that collect, use, or disclose personal information in the course of commercial activities, regardless of size or industry. This includes:
- Retail companies (online and physical stores collecting customer data for purchases or loyalty programs)
- Tech firms and SaaS providers (mobile app developers, cloud service providers processing user data)
- Professional service providers (law firms, accountants, consultants managing client records)
- Marketing and data analytics companies
- Financial services and insurance companies (especially those not already governed under specific legislation like the Bank Act).
A small online boutique collecting customer names, addresses, and payment info for e-commerce must comply with PIPEDA — even if it operates with only three employees.
✅ Organizations Operating Across Provincial or National Borders. PIPEDA specifically applies when personal information crosses provincial or national borders for processing or business purposes.
A Toronto-based CRM software company that hosts data on servers in the U.S. or interacts with clients in Quebec and Alberta must ensure PIPEDA compliance for that cross-border flow of data.
✅ Federally Regulated Organizations. Some industries fall under federal jurisdiction, meaning PIPEDA applies nationwide, regardless of local privacy laws. This includes:
- Banks and credit unions
- Airlines and railways
- Telecommunications companies
- Interprovincial trucking
- Radio and television broadcasters.
These organizations must apply PIPEDA to all personal information handling, even within provinces that have their own privacy legislation.
✅ Businesses in Provinces Without "Substantially Similar" Legislation. PIPEDA acts as a default privacy law in provinces and territories that don't have their own privacy laws deemed “substantially similar” by the federal government. Currently, only the following provinces have such laws for private-sector data handling:
- Quebec — Law on the Protection of Personal Information in the Private Sector
- British Columbia — Personal Information Protection Act (PIPA)
- Alberta — Personal Information Protection Act (PIPA).
📝 In these provinces, PIPEDA remains in effect for personal data transferred across provincial or international borders.
✅ Third-Party Service Providers and Vendors. Even if your organization does not collect data directly, you may fall under PIPEDA as a data processor or service provider. If you handle, store, or analyze personal data on behalf of a PIPEDA-covered organization, you are contractually and legally bound to comply with PIPEDA standards for safeguarding that data.
A cloud-hosting provider or payroll processing company acting on behalf of a retail chain must ensure adequate security and data handling in compliance with PIPEDA.
The Privacy Commissioner can investigate and recommend actions, but cannot fine directly under PIPEDA. Fines go through federal court. Financial penalties of up to CAD 100,000 per violation apply to:
- Negligent security practices
- Failing to report breaches
- Inadequate breach recordkeeping
- Tampering with investigations or obstructing complaints
Unlike GDPR, PIPEDA currently caps fines for individual violations, but proposed legislation (Bill C‑27) could raise penalties to:
- Administrative fines up to CAD 10 million or 3% of global revenue
- Criminal fines up to CAD 25 million or 5% of global revenue.
Companies like Oculus and Home Depot have been subject to investigations and public scrutiny under PIPEDA.
PIPEDA Compliance Checklist
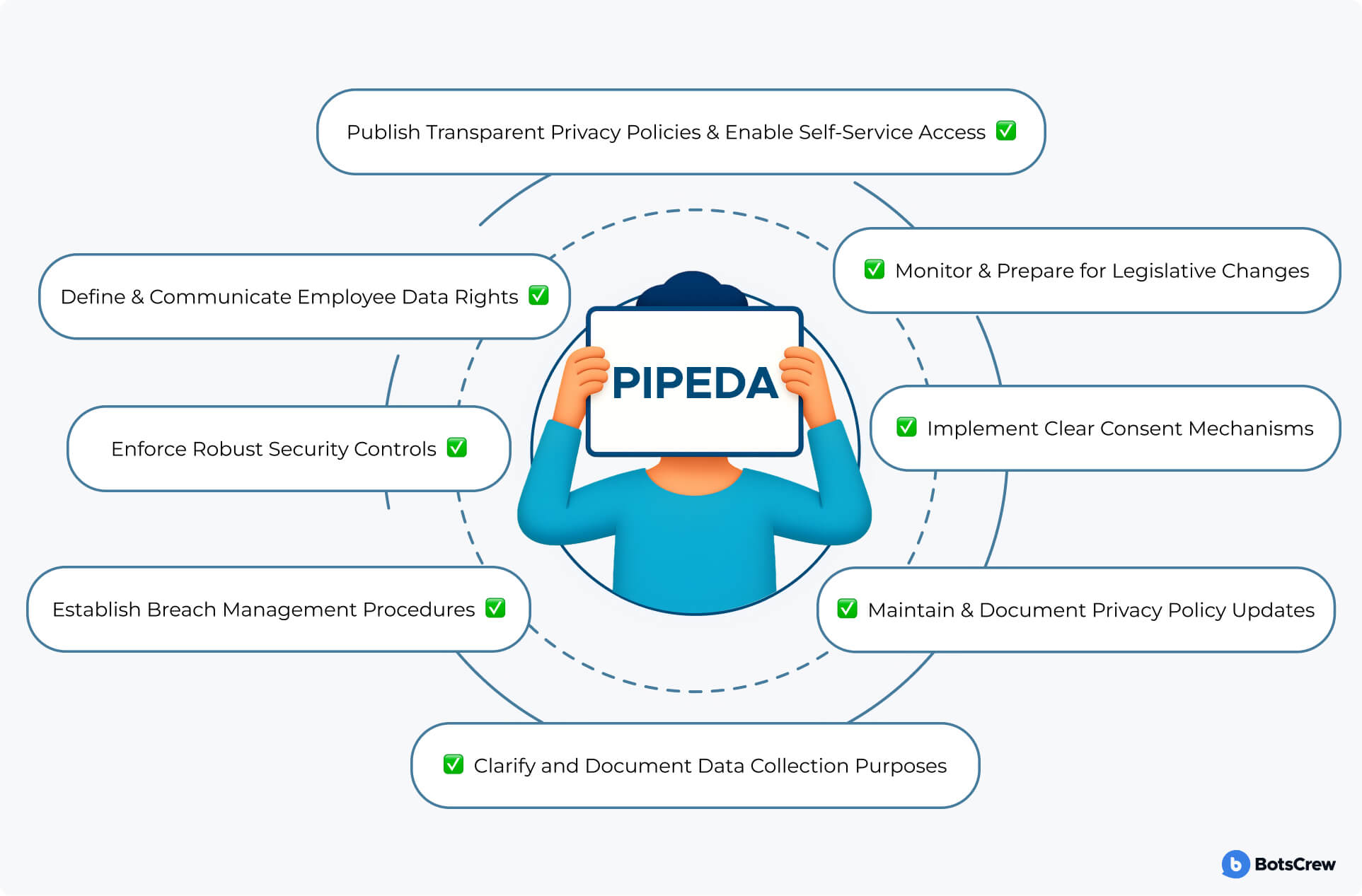
To keep your organization fully compliant and demonstrate accountability under Canada's federal privacy law, use this detailed checklist as your guide:
#1. Clarify and Document Data Collection Purposes. Define explicit purposes for every piece of personal information you collect. Collect only what's necessary to fulfill that purpose — nothing “just in case.” Document each purpose in your privacy policy and internal data inventory.
#2. Implement Clear Consent Mechanisms. Use clear, explicit opt-in mechanisms, avoiding pre-checked boxes or implied consent. Record the time, method, and scope of each individual's consent. Provide an easy way for people to withdraw consent and stop further use of their data.
#3. Publish Transparent Privacy Policies & Enable Self-Service Access. Make your privacy policy clear and easy to understand, detailing what data you collect, why you collect it, and who you share it with. Ensure individuals can view and correct their own records on request — ideally through a self-service portal. Outline in your policy how long you retain different data types and why.
#4. Enforce Robust Security Controls. Encrypt personal data at rest and in transit using industry-standard protocols. Implement role-based access controls so only authorized staff can reach sensitive records. Schedule regular system audits and vulnerability scans; document and remediate any gaps.
#5. Define & Communicate Employee Data Rights. Define clear access levels for HR, IT, and other teams — limit each to what they need. Communicate employees' rights to review or correct personal information held by the company. Incorporate these rights into your onboarding and exit processes.
#6. Establish Breach Management Procedures. Develop and test an incident response plan with clear roles, timelines, and communication templates. Report any breach posing a “real risk of significant harm” to both the Privacy Commissioner and affected individuals “as soon as feasible.” Maintain a breach log — record every incident (even minor ones) and your follow-up actions.
#7. Maintain & Document Privacy Policy Updates. Review and update your privacy policy at least annually, or whenever your data practices change. Publish change-logs or “last updated” dates so users know you are keeping pace with new requirements. Archive prior versions for accountability.
#8. Monitor & Prepare for Legislative Changes. Monitor emerging privacy legislation (e.g., Bill C-27) and assess how proposed changes — like higher fines or new rights — will affect you. Build flexibility into your programs so you can quickly adopt new rules without a complete overhaul. Engage legal or privacy consultants to interpret complex updates and guide your roadmap.
What is CCPA?
The California Consumer Privacy Act (CCPA) went into effect on January 1, 2020, granting Californians new rights over their personal data — from knowing what is collected about them to requiring its deletion. Voter-approved amendments under the California Privacy Rights Act (CPRA) expand those rights further, adding:
- “Sensitive Personal Information” protections (precise geolocation, race, health data)
- A new “Right to Correction”
- Mandatory risk assessments and contractor audits for high-risk data use.
CPRA's provisions take effect on January 1, 2023, and enforcement shifts from the Attorney General’s office to California's newly created Privacy Protection Agency.
Who Must Comply with CCPA/CPRA?
Any for-profit entity doing business in California that meets one or more of these thresholds must comply:
✅ Annual gross revenue > $25 million
✅ Buy, receive, or sell personal data of 50,000 or more California households, consumers, or devices per year
✅ Derive ≥ 50% of annual revenue from selling consumers' personal information
✅ Under CPRA, businesses handling > 4 million California consumers' personal data have additional obligations (e.g., risk assessments).
📝 Non-profits, government agencies, and most small businesses fall outside CCPA's scope — unless they meet the criteria above or sell data on behalf of covered entities.
Civil Penalties (per violation): $2,500 for unintentional violations or $7,500 for intentional or knowing violations.
Consumers can also sue businesses directly for breaches of unsecured personal data, seeking $100–$750 per incident or actual damages, whichever is higher.
CCPA/CPRA Compliance Checklist
Whether your business is based in California or simply serves California residents, use this as a practical guide to implementing practices that put privacy first:
#1. Map Your Data Flows & Inventory. Identify all personal data collected, stored, sold, or shared. Flag any “sales” under CCPA's broad definition (including free ad tech exchanges).
#2. Publish a CCPA-Compliant Privacy Notice. Include “Do Not Sell My Personal Information” link on your main page. Detail every data category, purpose, and third-party recipient.
#3. Build Clear Opt-Out & Rights-Request Processes. Implement a simple web form or toll-free number for data-access, deletion, and opt-out requests. Train staff to handle requests within 45 days (extendable once by 45 days).
#4. Update Contracts & Vendor Agreements. Ensure any third party “selling” or “sharing” data signs an addendum committing to CCPA/CPRA compliance. Make certain vendors support consumer data requests and cooperate with data audits.
#5. Implement Strong Security Safeguards. Encrypt data at rest and in transit. Regularly review your cybersecurity posture. Document breach-response plans, including notification templates to AG and consumers.
#6. Monitor Thresholds & Re-Evaluate Annually. Automate tracking of user-base size, revenue sources, and data-sharing volumes. If you exceed any threshold, initiate a comprehensive compliance review.

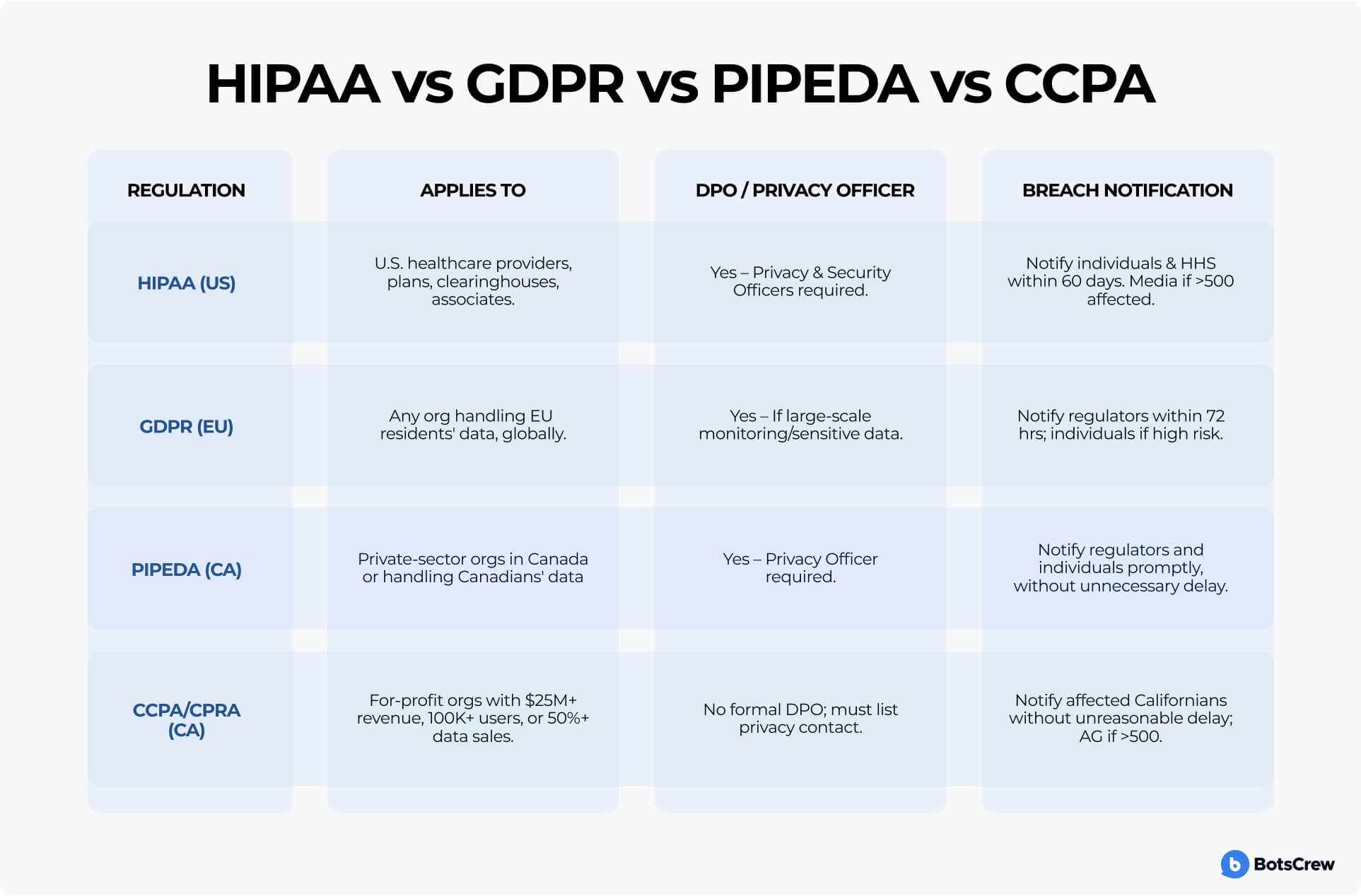
Comparing HIPAA, GDPR, PIPEDA & CCPA
While each law has a unique focus — healthcare, consumer rights, or commercial activity — they share common ground in requiring transparency, accountability, and swift action during data breaches. This comparison outlines key similarities and differences to help you understand which regulations apply, what roles must be designated, and how to respond to a breach under each law:
Want to Make Your Privacy Even Stronger?
Healthcare providers, insurers, and digital health innovators face growing pressure to protect sensitive data while complying with complex, evolving regulations like HIPAA, GDPR, and CCPA. The stakes are high — data breaches cost millions, erode trust, and can shut down operations. Yet, compliance doesn't have to be complicated or hold you back.
As experienced AI solution developers, we at BotsCrew build secure, privacy-first systems that meet the highest standards from day one. No shortcuts. No patchwork fixes. Just intelligent, compliant, and scalable solutions designed with privacy at the core.
✅ We know the laws — and keep your solution aligned with the latest regulatory updates.
✅ We act fast — with 24/7 monitoring, vulnerability scans, and real-time alerts.
✅ We build trust — with end-to-end encryption, anonymization/pseudonymization, and more.
Let us simplify the complex so you can focus on care, not compliance.
👉 Partner with a team that takes your security as seriously as you do.









